LAB401 ACADEMY: Mifare Cracking: Reader Attack with Chameleon Mini RevE Rebooted INTRODUCTION: Lab401's Chameleon Mini RevE Rebooted is a compact, highly capable tool typically used for 13.56MHz emulation (Mifare, Ultralight, etc). When a reader begins communication with a Mifare Tag, it will send a series of keys to attempt card decryption.
Nowadays, this attack is not covering a lot of Mifare classic card anymore. The Proxmark is the best choice. For the Proxmark3, the weak PRNG method is easy to find but the sniff/hardnested method for hard PRNG is more tricky. First Of All – Try Generic Keys like this somekeys.txt, took from Mifare Classic Tool (android). Jul 24, 2018 Mifare Classic Offline Cracker. Contribute to nfc-tools/mfoc development by creating an account on GitHub.
Hacking MIFARE & RFID
As we start this series, you won’t find anything that hasn’t already been discussed before. This is not a new topic, but rather my own vision of the many different things that’ve been done concerning RFID. Other Proof of Concepts (PoCs) I’ve read were not so thorough, this is my attempt at being more thorough so others have a better understanding.
The main goal
The goal here is to cover the process of cloning and editing RFID tags. MIFARE Classic ones especially, which are still widely used nowadays despite the many hacks found throughout the last few years. This is not intended to teach you all about RFID, NFC, and MIFARE hacking. So, before we jump in let’s learn some basics.

RFID, NFC & MIFARE : The Basics
Radio Frequency Identification (RFID), is a technology that uses electromagnetic fields to automatically identify and/or track “tags” that contain electronically stored information. Some tags are passive, therefore they are activated by the electromagnetic fields generated by nearby readers. Some tags are active and require a local power source, such as a battery. They are capable of operating hundreds of meters from the closest RFID reader. The use of RFID always implies three things:
Mifare Cracking Iphone
- a tag
- a reader
- an antenna (ranging from Low to High and Ultra High frequencies)
Near Field Communication (NFC), is a set of communication protocols. These protocols enable two electronic devices to trade information within 4 centimeters (~2 inches) of each other. NFC operates within the same range of frequencies of RFID. NFC was created as a new way of communicating with other RFID tags.
NFCs main purpose was to break out of the standard tag/reader “read-only” pattern. This is to allow both devices to become reader, antenna, and tag.
MIFARE, is a trademark for a series of chips widely used in contactless smart cards and proximity cards. It is often incorrectly used as a synonym of RFID. MIFARE is owned by NXP semiconductors which was previously known as Philips Electronics.
The reason behind this misuse is simple. MIFARE chips represent approximately 80% of the RFID passive tags in the world.
Think of MIFARE as being the most used type of RFID tags. NFC is simply a newer technology to interact with the first two. With that little bit of knowledge, let’s focus on MIFARE. The MIFARE family is split into subcategories which can be briefly describe here:
- MIFARE Classic 1K/4K: basically just a memory storage device. This memory, either 1024 or 4096 bytes, is divided into sectors and blocks. Most of the time used for regular access badges and has reaaally simple security mechanisms for access control
- MIFARE Ultralight: a 64 bytes version of MIFARE Classic. It’s low costs make it widely used as disposable tickets for events or transportation.
- MIFARE Plus: announced as a replacement of MIFARE Classic. The Plus subfamily brings the new level of security up to 128-bit AES encryption.
- MIFARE DESFire: those tags come pre-programmed with a general purpose DESFire operating system which offers a simple directory structure and files, and are the type of MIFARE offering the highest security levels.
Where my research comes in…
In 2018, my employer started handing out U-KEYs to be used to load funds onto and buy coffee and snacks from different vending machines around the building. With this being 2019, contactless payment is becoming more common with your credit cards/smartphones. These technologies have gone through rigorous testing to ensure users data is securure and so far it’s pretty solid, but what about these little keys?
Mifare Crack
Turns out with a little bit of research, those keys are simply MIFARE Classic 1K and the associated security mechanisms are actually quite simple. But how simple?
Breaking down MIFARE Classic tag structure
This classic tag structure is a whopping 1,024 bytes in size. Those 1,024 bytes are split into 16 sectors (0 to 15) which are each split into 4 blocks (0 to 3). That’s 16 bytes on each row (Figure 1.1). When we get into modifying data our focus will be a certain byte of data in the 7th byte of the 2nd block of the sector 13.
Every sector has a common structure: 3 blocks of data, and 1 “access control” block. The access control blocks contain Key A, Key B, and the Access Bits. See (Figure 1.2) The A & B keys can be standard (as in the most commonly used) or unique and set by the tag owner, and the access bits determine the rights on each sectors (read, write, both or none).
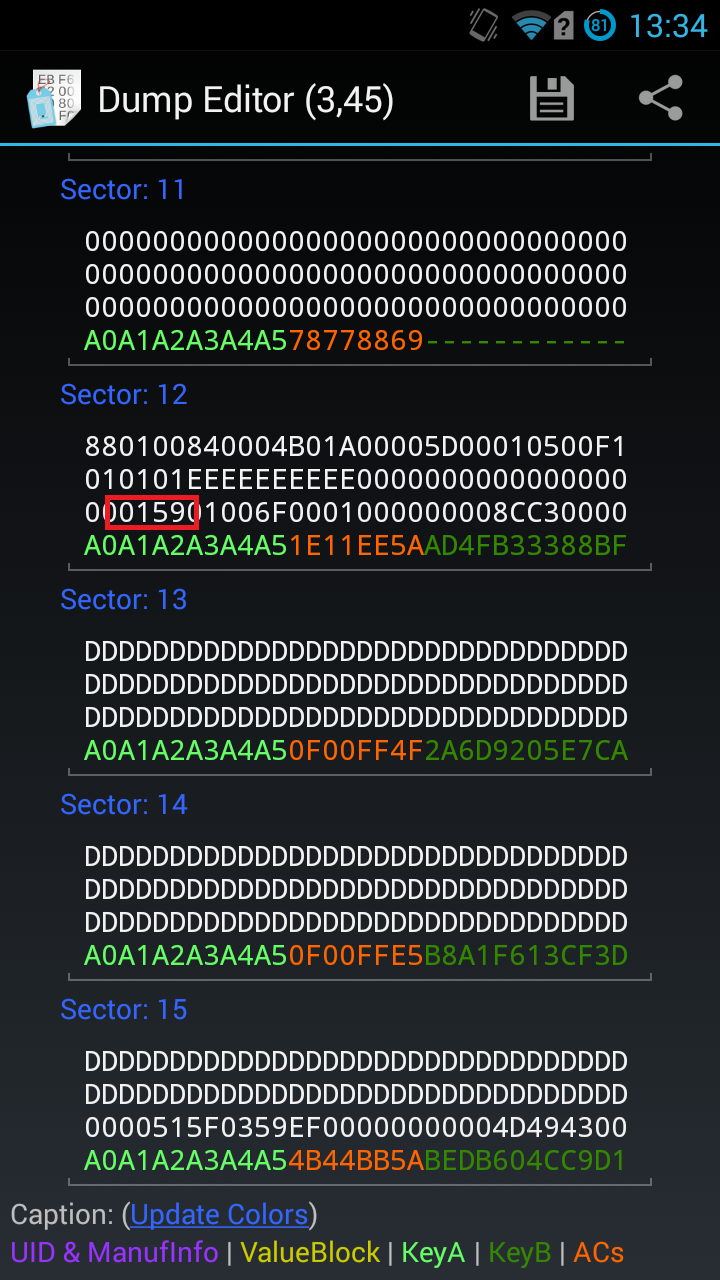
Moving forward, the only different sector will be sector 0, block 0. This one does not have an access control block but rather a manufacturer block instead. This is where the tag’s manufacturers can store an unique ID (UID) and information like the date of creation. The Manufacturer block is a Read-Only block. Manufacturers do not want end users to modify their data (Figure 1.3).
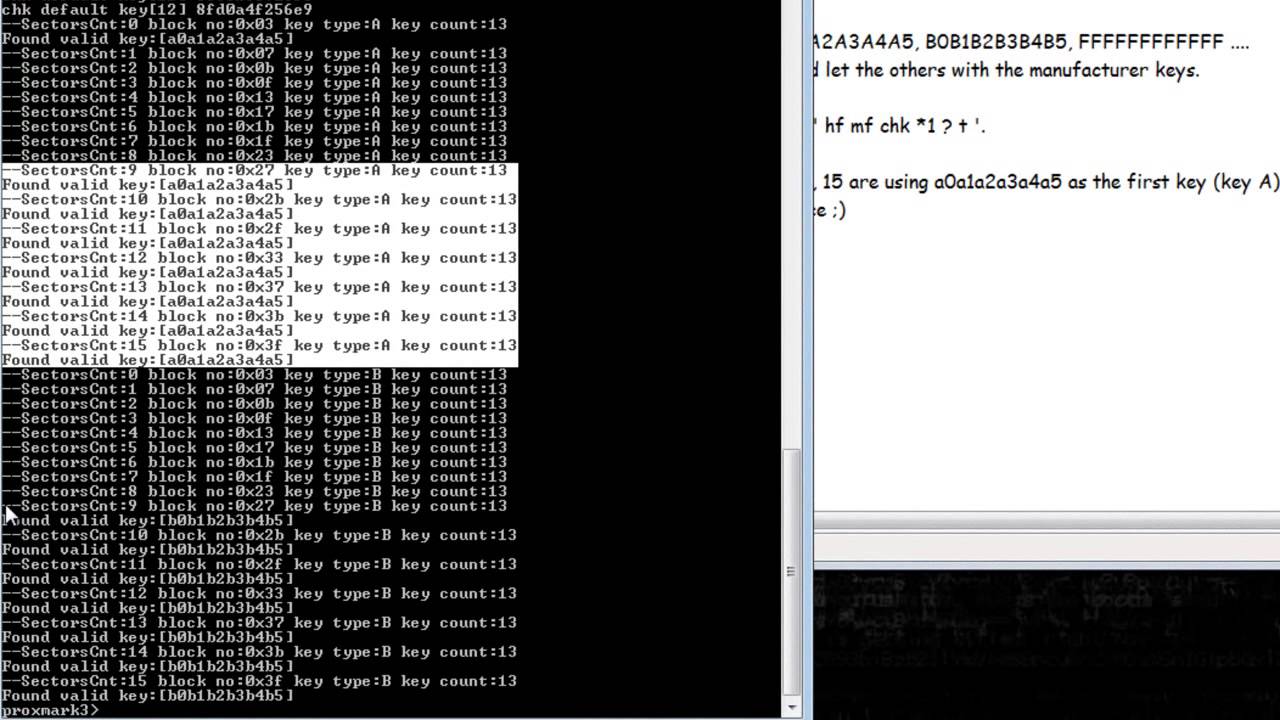
Knowing how memory is stored, how can it be read? And more importantly, how can it be modified? When we present the tag to a reader, the reader sends a POR (PowerOn Reset). This will get our tag out of its “sleep” passive mode. If the sent request is standard, the tag and the reader will start to communicate and share an encrypted session key. (Figure 2.1)
These operations on a tag are quite simple, visible in Figure 2.1:
- AUTHENTICATE
- READ/WRITE/DECREMENT/INCREMENT – always sent in encrypted session.
- TRANSFER – writes the result of one of the previous operations to non-volatile memory.
- RESTORE – prepares the current value of blocks to be over-written.
Moving on from here, you might have a few questions. Some that come to mind are:
- How strong is this encrypted session?
- Is that encryption crackable?
- Does the tag have any way of checking the modification requests sent from a legitimate reader?
- Can we spoof those requests to modify it with our own data?
Check out the next article if you want your answers. =D
We provide our customers with a variety of tools, giving them the possibility to enlarge the variety of service they deliver:
- TapLinx: Android based development kit that allows to create a mobile application reading MIFARE cards in no time
- RFIDDiscover – NXP’s 13,56 MHz contactless IC products expert tool
- NFC TagInfo App by NXP, available in the Google Play Store, helps you to check which MIFARE product is in a card
- NFC TagWriter App by NXP stores contacts, bookmarks, SMS, Mail, text messages and many more to any NFC-enabled tag
Tools that can help to verify the originality of MIFARE ICs:
- Application Notes to implement Originality Signature Verification in customer applications
- Dedicated functions in TapLinx
- NFC TagInfo App by NXP, available in the Google PlayStore
- Analysis in the Lab
TapLinx
Your simple way to cool Apps
RFIDDiscover
Mifare Cracking Video
NXP’s 13,56 MHz contactless IC products expert tool
Reader-Writer Kit for MIFARE ICs
Includes the Pegoda II reader writer, sample tags and required software
NXP Originality Checker Reader
Mifare Cracking Windows

Helps to verify the authenticity of a MIFARE IC
NFC TagInfo App by NXP
Get more information about your NFC tag
NFC TagWriter App by NXP
Write your own NXP NFC tags
Cracking Mifare Ultralight
Please note, the tools listed on this page may help you to verify the authenticity of a MIFARE IC and NXP shall not be liable for the information provided. For more information please contact MIFARE@nxp.com.