- Internal audit Are internal audits conducted periodically to check that the ISMS is effective and conforms to both ISO/IEC and the organization’s requirements? Are the audits conducted by an appropriate method and in line with an audit programme based on the results of risk assessments and previous audits?
- Iso 27002 Audit Checklist Xls Francais ISO/IEC gives guidelines for organizational information security standards and information security management practices including the selection, implementation and management of controls taking into consideration the organization's information security risk environment(s).
ISO 27001; 2013 transition checklist ISO 27001: 2013 – requirements Comments and evidence 0 Introduction 0.1 General There are some textural changes for example the new standard are “requirements” for an ISMS rather than “a model for”. Generally these do not affect the purpose of the standard. ISO27001 Checklist tool – screenshot. As mentioned previously, we have now uploaded our ISO 27001 (also known as ISO/IEC ) compliance checklist and it is available for free download. Please feel free to grab a copy and share it with anyone you think would benefit.
If you are planning your ISO 27001 audit, you may be looking for some kind of an ISO 27001 audit checklist, such a as free ISO PDF Download to help you with this task.
Although they are helpful to an extent, there is no tick-box universal checklist that can simply be “ticked through” for ISO 27001 or any other standard.
Every company is different. And if an ISO management system for that company has been specifically written around it’s needs (which it should be!), each ISO system will be different. The internal auditing process will be different. We explain this in more depth elsewhere in our blogs. You could always call us, too!
However, you can create your own basic ISO 27001 audit checklist, customised to your organisation, without too much trouble. Read on to find out how.
Basics
By the way, We’re taking a broad, simple approach in this blog. But for the best results, we’d recommend some training to make the whole process much easier. However, sharing some basics will, at least, demystify the process and provide a basic framework.
And these broad principles are applicable for internal audit of other standards, such as ISO 9001, ISO 14001, etc.:
So, some basic steps in the process:-
Document review.
Quite simple! Read your Information Security Management System (or part of the ISMS you are about to audit). You will need to understand processes in the ISMS, and find out if there are non-conformities in the documentation with regard to ISO 27001. A call to your friendly ISO Consultant might help here if you get stuck(!)
Creating the checklist.
Also quite simple – make a checklist based on the document review, i.e., read about the specific requirements of the policies, procedures and plans written in the documentation and write them down so that you can check them during the main audit. For example, if the data backup policy requires the backup to be made every 6 hours, then you have to note this in your checklist in order to check if it really does happen. Take time and care over this! – it is foundational to the success and level of difficulty of the rest of the internal audit, as will be seen later.
Planning the main audit.
Or “make an itinerary for a grand tour”(!) . Plan which departments and/or locations to visit and when – your checklist will give you an idea on the main focus required.
Performing the main audit.
It is astonishingly practical! Walk around the company talk to staff, check computers and other equipment, observe physical security, etc. Your previously-prepared ISO 27001 audit checklist now proves it’s worth – if this is vague, shallow, and incomplete, it is probable that you will forget to check many key things. And you will need to take detailed notes.
Reporting.
Summarize all the non-conformities and write the Internal audit report. With the checklist and the detailed notes, a precise report should not be too difficult to write. From this, corrective actions should be easy to record according to the documented corrective action procedure.
Follow-up.
It’s the internal auditor’s job to check whether all the corrective actions identified during the internal audit are addressed. The checklist and notes from “walking around” are once again crucial as to the reasons why a nonconformity was raised. The internal auditor’s job is only finished when these are rectified and closed, and the ISO 27001 audit checklist is simply a tool to serve this end, not an end in itself!
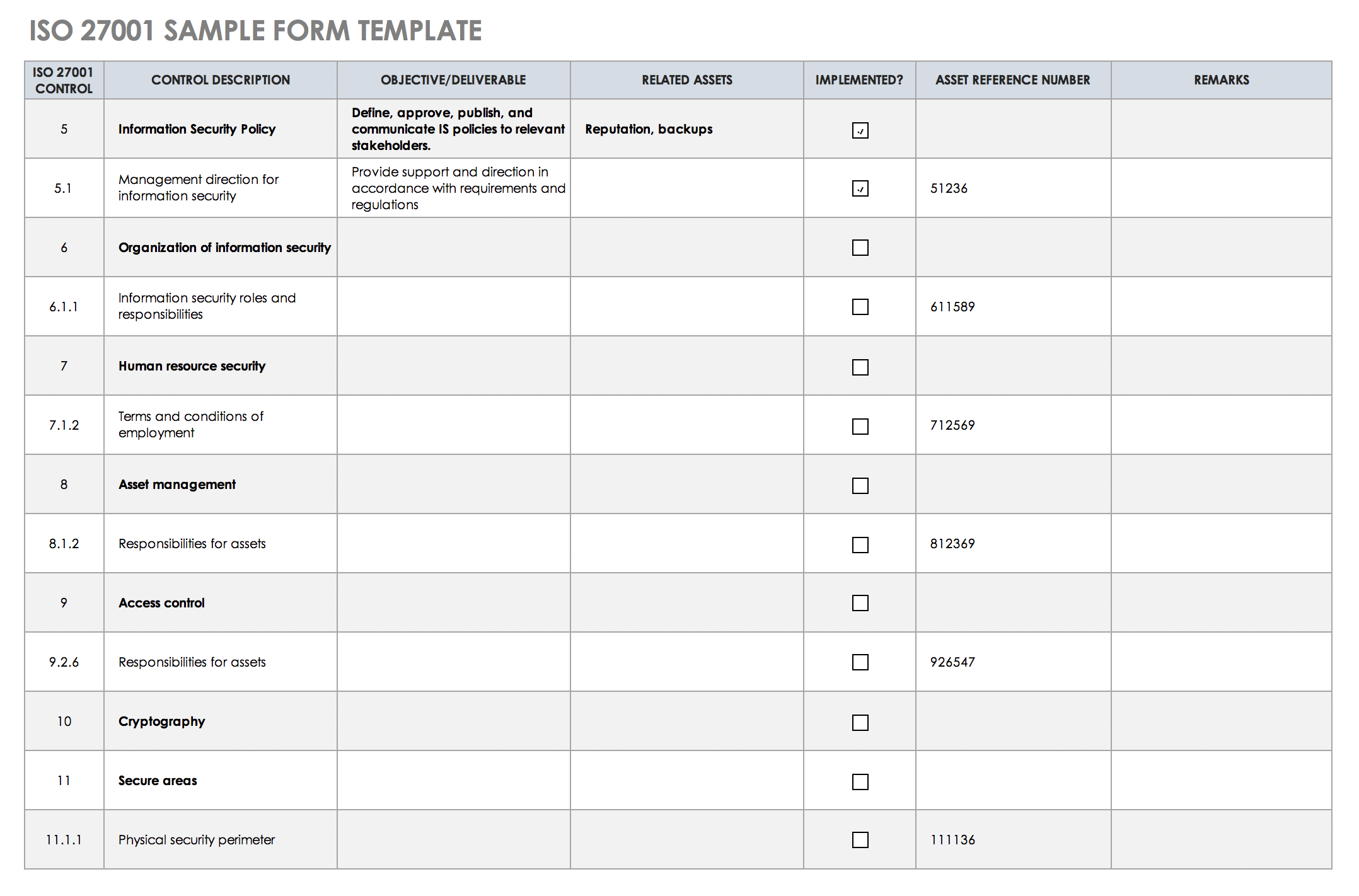

Checklist Format – Some Basic Guidelines
A suggestion to aid simplicity! We’d recommend 4 columns as follows:-
Reference– e.g. the clause number, section number of a policy, within the standard.
What to look for– what to examine, monitor, etc., during the main audit – whom to speak to, which questions to ask, records to look for, facilities to visit, equipment to check, etc.
Compliance– Simply, has the company has complied with the requirement? Yes or No, or occasionally “not applicable”.
Findings – Details of the more-specific “findings” of the main audit I.e. staff spoken to, quotes of what they said, IDs and content of records examined, description of facilities visited, observations about the equipment checked, etc.
So,the internal audit of ISO 27001, based on an ISO 27001 audit checklist, is not that difficult – it is rather straightforward: you need to follow what is required in the standard and what is required in the documentation, finding out whether staff are complying with the procedures.
With a good ISO 27001 audit checklist audit checklist, your task will certainly be a lot easier.
And if you need our help, or even want us to run some training for you, please drop us a line! .
- Ankita on 3rd June 2016 at 13:41
Great strategies you shared. Smartpls 3 with crack. I am new to the scene. I will be implementing these tomorrow. Thanks!
We’re not going to lie: implementing an ISO 27001-compliant ISMS (information security management system) can be a challenge.
But as the saying goes, nothing worth having comes easy, and ISO 27001 is definitely worth having.
If you’re just getting started with ISO 27001, we’ve compiled this 9 step implementation checklist to help you along the way.
Step 1: Assemble an implementation team
Your first task is to appoint a project leader to oversee the implementation of the ISMS.
Iso 27001 2013 Checklist
They should have a well-rounded knowledge of information security as well as the authority to lead a team and give orders to managers (whose departments they will need to review).
The team leader will require a group of people to help them. Senior management can select the team themselves or allow the team leader to choose their own staff.
Once the team is assembled, they should create a project mandate. This is essentially a set of answers to the following questions:
- What are we hoping to achieve?
- How long will it take?
- How much will it cost?
- Does the project have management support?
Step 2: Develop the implementation plan

Next, you need to start planning for the implementation itself.
The implementation team will use their project mandate to create a more detailed outline of their information security objectives, plan and risk register.
This includes setting out high-level policies for the ISMS that establish:
- Roles and responsibilities.
- Rules for its continual improvement.
- How to raise awareness of the project through internal and external communication.
Step 3: Initiate the ISMS
With the plan in place, it’s time to determine which continual improvement methodology to use.
ISO 27001 doesn’t specify a particular method, instead recommending a “process approach”. This is essentially a Plan-Do-Check-Act strategy
You can use any model as long as the requirements and processes are clearly defined, implemented correctly, and reviewed and improved on a regular basis.
You also need to create an ISMS policy.
This doesn’t need to be detailed; it simply needs to outline what your implementation team wants to achieve and how they plan to do it.
Once it’s completed, it should be approved by the board.
At this point, you can develop the rest of your document structure. We recommend using a four-tier strategy:
- Policies at the top, defining the organisation’s position on specific issues, such as acceptable use and password management.
- Procedures to enact the policies’ requirements.
- Work instructions describing how employees should meet those policies.
- Records tracking the procedures and work instructions
Step 4: Define the ISMS scope
The next step is to gain a broader sense of the ISMS’s framework. The process for doing this is outlined in clauses 4 and 5 of the ISO 27001 standard.
This step is crucial in defining the scale of your ISMS and the level of reach it will have in your day-to-day operations.
As such, it’s obviously important that you recognise everything that’s relevant to your organisation so that the ISMS can meet your organisation’s needs.
The most important part of this process is defining the scope of your ISMS. This involves identifying the locations where information is stored, whether that’s physical or digital files, systems or portable devices.
Defining your scope correctly is an essential part of your ISMS implementation project.
If your scope is too small, then you leave information exposed, jeopardising the security of your organisation. But if your scope is too large, the ISMS will become too complex to manage.
Step 5: Identify your security baseline
An organisation’s security baseline is the minimum level of activity required to conduct business securely.
You can identify your security baseline with the information gathered in your ISO 27001 risk assessment.
This will help you identify your organisation’s biggest security vulnerabilities and the corresponding controls to mitigate the risk (outlined in Annex A of the Standard).

Step 6: Establish a risk management process
Risk management is at the heart of an ISMS.
Almost every aspect of your security system is based around the threats you’ve identified and prioritised, making risk management a core competency for any organisation implementing ISO 27001.
The Standard allows organisations to define their own risk management processes. Common methods focus on looking at risks to specific assets or risks presented in specific scenarios.
Whatever process you opt for, your decisions must be the result of a risk assessment. This is a five-step process:
- Establish a risk assessment framework
- Identify risks
- Analyse risks
- Evaluate risks
- Select risk management options
You then need to establish your risk acceptance criteria, i.e. the damage that threats will cause and the likelihood of them occurring.
Managers often quantify risks by scoring them on a risk matrix; the higher the score, the bigger the threat.
They’ll then select a threshold for the point at which a risk must be addressed. Download free macos catalina 10.15 mac dmg.
Audit Checklist Template
There are four approaches you can take when addressing a risk:
- Tolerate the risk
- Treat the risk by applying controls
- Terminate the risk by avoiding it entirely
- Transfer the risk (with an insurance policy or via an agreement with other parties).
Lastly, ISO 27001 requires organisations to complete an SoA (Statement of Applicability) documenting which of the Standard’s controls you’ve selected and omitted and why you made those choices.
Step 7: Implement a risk treatment plan
The implementation of the risk treatment plan is the process of building the security controls that will protect your organisation’s information assets.
To ensure these controls are effective, you’ll need to check that staff are able to operate or interact with the controls, and that they are aware of their information security obligations.
You’ll also need to develop a process to determine, review and maintain the competences necessary to achieve your ISMS objectives.
This involves conducting a needs analysis and defining a desired level of competence.
Step 8: Measure, monitor and review
You won’t be able to tell if your ISMS is working or not unless you review it.
We recommend doing this at least annually, so that you can keep a close eye on the evolving risk landscape
The review process involves identifying criteria that reflect the objectives you laid out in the project mandate.
A common metric is quantitative analysis, in which you assign a number to whatever you are measuring.
This is helpful when using things that involve financial costs or time.
The alternative is qualitative analysis, in which measurements are based on judgement.
You would use qualitative analysis when the assessment is best suited to categorisation, such as ‘high’, ‘medium’ and ‘low’.
In addition to this process, you should conduct regular internal audits of your ISMS.
The Standard doesn’t specify how you should carry out an internal audit, meaning it’s possible to conduct the assessment one department at a time.
This helps prevent significant losses in productivity and ensures your team’s efforts aren’t spread too thinly across various tasks.
However, you should obviously aim to complete the process as quickly as possible, because you need to get the results, review them and plan for the following year’s audit.
The results of your internal audit form the inputs for the management review, which will be fed into the continual improvement process.
Step 9: Certify your ISMS
Once the ISMS is in place, you may choose to seek certification, in which case you need to prepare for an external audit. Ex4 file to mq4.
Certification audits are conducted in two stages.
The initial audit determines whether the organisation’s ISMS has been developed in line with ISO 27001’s requirements. If the auditor is satisfied, they’ll conduct a more thorough investigation.
You should be confident in your ability to certify before proceeding, because the process is time-consuming and you’ll still be charged if you fail immediately.
Another thing you should bear in mind is which certification body to go for.
There are plenty to choose from, but you absolutely must make sure they are accredited by a national certification body, which should be a member of the IAF (International Accreditation Body).
This ensures that the review is actually in accordance with ISO 27001, as opposed to uncertified bodies, which often promise to provide certification regardless of the organisation’s compliance posture.
The cost of the certification audit will probably be a primary factor when deciding which body to go for, but it shouldn’t be your only concern.
You should also consider whether the reviewer has experience in your industry.
After all, an ISMS is always unique to the organisation that creates it, and whoever is conducting the audit must be aware of your requirements.
Tackling ISO 27001 implementation?
Even with the advice listed here, you might find the ISO 27001 implementation project daunting.
Nine Steps to Success – An ISO 27001 Implementation Overview is a “must-have” guide for anyone starting to implement ISO 27001.
It details the key steps of an ISO 27001 project from inception to certification and explains each element of the project in simple, non-technical language.